An ongoing research conducted by Avast’s Mobile Security Intelligence & Security Division, headed by Security Analyst, Nikolaos Chrysaidos, reveals the leak of sensitive data belonging to Greek citizens by an advanced version of the notorious Android Banking Trojan, BankBot.
Earlier this year we’ve reported the leak of the source code of a malicious banking malware for Android, along with instructions on how it could be used.
As expected, the code of the notorious mobile banking Trojan (also known as BankBot) was exploited by hackers and script kiddies to create and spread new and more sophisticated instances of this Trojan family.
Android users should be extremely careful with the apps they install on their mobile devices, as BankBot can be distributed as a popular application or can be injected into APKs available on the internet or into third-party stores. BankBot has already managed to enter Google Play’s marketplace.
The initial analysis of the first samples detected after the code leak shows that once the banking trojan infects an Android device and acquires root permissions, it remains hidden in the background and connects to a C&C server, awaiting for commands. BankBot can perform a bunch of malicious activities, such as sending and receiving SMS messages, stealing contacts, tracking devices, making calls, displaying phishing dialog and stealing sensitive information, such as banking and credit card details.
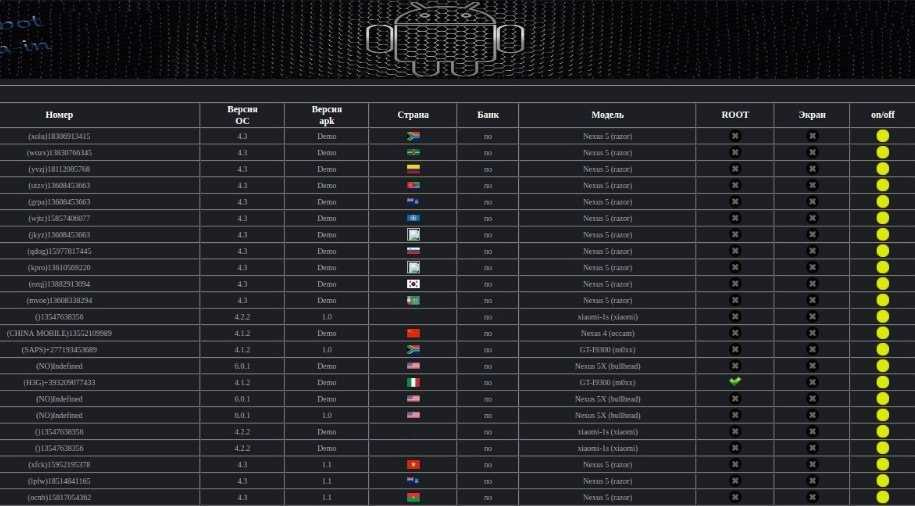
Below we can see the control panel of a recently discovered instance:
Sensitive data of Greek citizens leaked online
A recent survey conducted by Nikolaos Chrysaidos, head of mobile threat intelligence and security at Avast, reveals a significant number of sophisticated BankBot variants, that intercept victims’ banking details and sensitive data, like credit card numbers, CVCs etc, from their Android devices.
Among the databases discovered during the ongoing research, a database with sensitive personal data of Greek citizens has also been discovered.
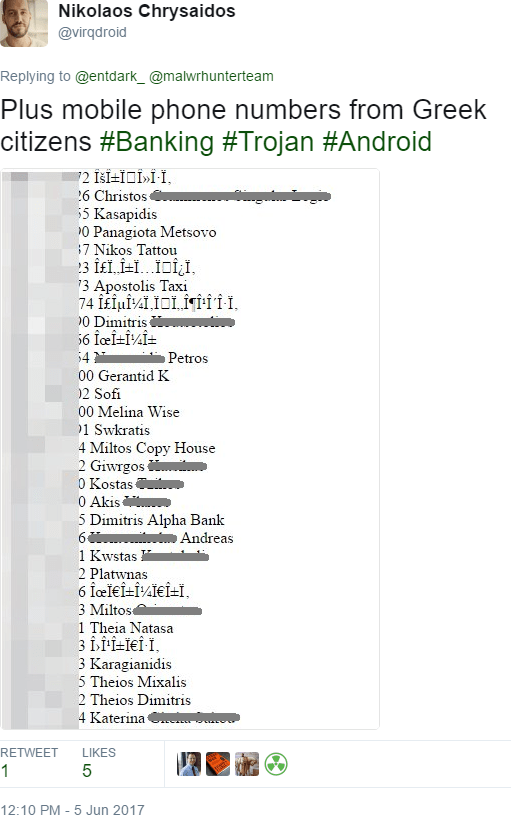
The data were found in an online un-protected C&C server that one BankBot family was using to store data exfiltrated from users mobile devices. The specific leak contains names and contact numbers from Greek citizens.
Below you can see a screenshot posted by Avast’s Analyst in his Twitter account (sensitive contents hidden):
It should be noted that this is only a small part of data leaked, as the database contains 392 records in total.
How does BankBot infect Android devices?
This mobile banking threat can infect users by the following means:
– By faking various legit applications (Banking Apps, Social Messaging Apps etc)
– It can be served through third-party stores, or as a link inside fraudulent emails or SMS text messages.
– Most commonly, cyber criminals are trying to convince users to install a package that appears as a System update, Flash Player etc.
How can be users be protected?
– Users should be very careful when downloading applications from links or stores, outside of the Google Play Store.
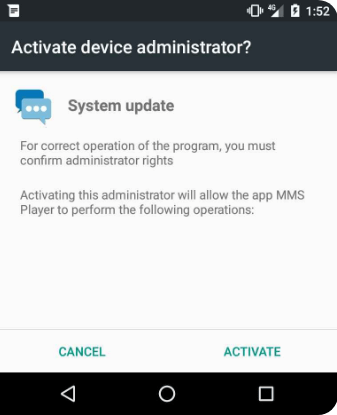
– Users should also be very cautious if they see the following screen, prompting to “Activate Device Administrator”, as most of the banking threats use this technique to become persistent and much more difficult to uninstall.
– In case a user has already activated it, he/she should go to Settings > Security > Device administrators and tap the suspicious application.
– Users should also be pro-active and use a mobile AV solution, always keeping it up-to-date.
We would like to thank Mr.Chrysaidos Nikolaos for the highly interesting information provided to SecNews editorial team.
About Nikolaos Chrysaidos:
Nikolaos is head of mobile threat intelligence and security at Avast, leading mobile security projects, mobile threat intelligence, and threat prevention. He loves mobile forensics, malware analysis, and reverse engineering.